Security is one of the major concerns in any field nowadays. And then comes the “Data security”. As the name indicates, it is a way to secure our data. One of the most common methods of practicing data security is the use of authentication. With authentication, users must provide a password, code, specific data, or some form of data to verify identity before access to a system or data is granted.
Nowadays, data security is an important aspect of IT companies of every size and type. It is important to get the right Data Security Solutions in order to meet challenging threats.
Levels of Data Access in Salesforce
Salesforce provides us an easy to handle and flexible data security model to secure data at different levels.
Salesforce also provides sharing tools to open and allow secure access to data-supported business needs that can control which user approach which information in our entire organization, an article, a particular field, or an individual record or any other data.
Organization
This is the basic level of security.
For the entire organization, we can keep a list of approved users, set password approaches, and limit logins to specific hours and/or areas and specific IP ranges.
Object-level-security
Object-level security protects data and gives access to data at the object level. By setting consents on a specific sort of item, we can keep a gathering of users from creating, viewing, altering, or erasing any records of that object. For instance, we can utilize object authorizations to guarantee that interviewers can see positions and employment applications however not alter or erase them.
Fields
Similarly, field-level security protects data and gives access to data at the field level. We can confine access to specific fields, regardless of whether a client approaches the item. For instance, we can make the compensation field in a position object imperceptible to interviewers however visible to procuring supervisors and enrolment specialists.
Records
Record level security protects data and gives access to data at the record level. We can enable specific users to see an item, yet then limit the individual article records that they’re permitted to see. For instance, an interviewer can see and alter her own surveys, yet not the audits of different interviewers.
You can oversee record-level access in these four different ways
Organization-wide sharing settings
The very first step in record-level security is to determine the organization-wide sharing settings for each object as it is the most basic level. We use the organization-wide sharing settings to secure our data to the most basic and restrictive level, and then use the other record-level security and sharing tools to selectively give access to other users.
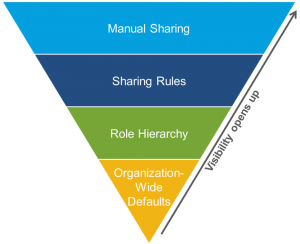
Role hierarchy
Once we’ve specified organization-wide sharing settings, the first way we can give wider access to records is with a role hierarchy. A role hierarchy represents data access at a level, that a user or group of users needs. The role hierarchy gives a surety that the users that are higher in the hierarchy always have access to the data the same as people lower in their hierarchy, regardless of the organization-wide default settings.
Role hierarchies don’t have to match our organization chart exactly, each role in the hierarchy should represent a level of data access that a user or group of user’s needs. Well, it’s easy to confuse permission sets and profiles with roles, but they control two very different things. It (confuse permission sets and profiles) control a user’s object and field access permissions. Here roles control a user’s record-level access through role hierarchy and sharing rules.
Sharing rules
Sharing rules help us in making automatic exceptions to organization-wide sharing settings for sets of users, to give them access to records they don’t own or can’t normally see. Sharing rules, like role hierarchies, are only used to give additional users access to records—they can’t be stricter than our organization-wide default settings.
Manual sharing
At some point of time, it’s impossible to define a consistent group of users who need access to a set of records. At that point, record owners can use manual sharing to give read and edit permissions to users who would not have access to the record any other way. Unlike the above three mentioned rules, manual sharing isn’t automated, it gives record owners the flexibility to share records with users that need to see them.
Leave A Comment