
OAuth 2.0 provides an authentication flow for web and desktop applications and mobile devices. OAuth 2.0 provides authorized access and limits the actions that client apps can perform on resources on behalf of the user without sharing the user’s credentials.
The Web is the main platform for OAuth2, but this specification extends this type of delegated access to other client types (browser-based applications, server-side web applications, native / mobile apps, connected devices, etc.).
Scope is an important concept in OAuth 2.0. These are used to specify the exact reason why access to the resource can be granted. The tolerance values and the resources they refer to depend on the resource server.
OAuth defines four roles.
- Resource Owner: A resource owner is a user who grants application access to their account. Application access to user accounts is restricted to the scope of permissions granted (such as read or write access).
- Client: A client is an application that wants to access a user’s account. Before that, it needs to be approved by the user, and the approval needs to be validated by the API.
- Resource Server: The resource server hosts a protected user account.
- Authorization server: The authorization server verifies the user’s identity and then issues an access token to the application.
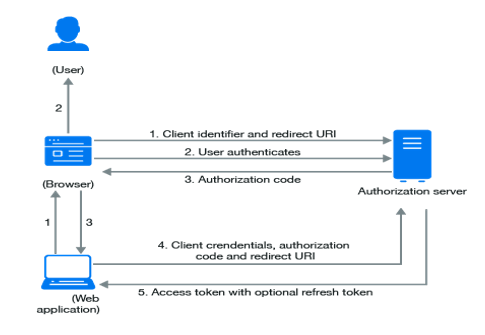
When using OAuth 2.0, the access request is initiated by the client’s Mobile apps, websites, smart TV apps, desktop applications and more. OAuth2.0 uses two endpoints, the /authorize endpoint, and the /oauth /token endpoint. Requesting, exchanging, and responding to tokens follows the general flow below:
GET/Authorize
1. The client requests authorization (authorization request) from the authorization server and provides the client ID and secret as the ID. It also provides the scope and endpoint URI (redirect URI) to which the access token or authorization code will be sent. To get the Authorization Code using Client ID and add the redirect URI in the request.
Method: GET
https://YOUR_DOMAIN/authorize?audience=API_IDENTIFIER&scope=SCOPE&response_type=code&client_id=YOUR_CLIENT_ID&redirect_uri=https://YOUR_APP/callback&state=STATE
Request Formation – URL based request
https://domain/authorize?response_type=code&client_id=clientID&connection=&redirect_uri=redirectApplicationUrl
The Authorization code will be returned by the server getting appended to redirectURI with keyword code.
Redirect URI:
The redirect URI is an important part of the OAuth flow. If the user successfully approves the application, the approval server redirects the user to the application. It is important that the service does not redirect the user to any location, as the redirect URI contains sensitive information. The authorization server authenticates the client and verifies that the requested scope is valid.
POST/oauth/tokenPOST/oauth/token
2. The resource owner interacts with the authorization server to grant access. As described in the next section, the authentication server returns to the client using either an authentication code or an access token, depending on the type of grant. You can also return an update token. The client uses the access token to request access to the resource from the resource server.
The app will request Access Token. Using API Key in the header and the authorization code received in the previous step, the request will be formed and sent to external applications.
API Callout for AccessToken:
Method: POST
Header: Content-Type: application/x-www-form-urlencoded
EndPoint: https://domain.auth0.com/oauth/tokengrant_type=authorization_code&client_id=YOUR_CLIENT_ID&client_secret=YOUR_CLIENT_SECRET&code=AUTHORIZATION_CODE&redirect_uri=https://YOUR_APP/callback
3. The next step after getting an access token will be to obtain the User Information from the Application. A request will be made to application as soon as the access token request is successful to fetch the Org Code and Org Id. The relevant data from response of API callout will be stored in the salesforce custom settings.
API Callout for User Info:
Method: GET
Header: Authorization: Bearer AccessToken(Obtained from previous step)
Endpoint: https://domain.auth0.com/userinfo
Conclusion:
OAuth 2 is an authentication framework that allows applications such as Facebook, GitHub, and Digital Ocean to restrict access to user accounts for HTTP services. OAuth 2.0 is an authorization protocol, not an authentication protocol. Therefore, it is primarily designed as a means of granting access to various resources Remote API or user data. It replaced OAuth 1.0 in 2012 and is now OAuth 2.0 provides authorized access and limits the actions that client apps can perform on resources on behalf of the user without sharing the user’s credentials.
Leave A Comment